A malware campaign spreading a clipboard hijacker has infected over 300,000 computers, according to Chinese security firm Qihoo 360 Total Security.
The campaign has been raging for the past week and has spread a malware which Qihoo researchers have named ClipboardWalletHijacker.
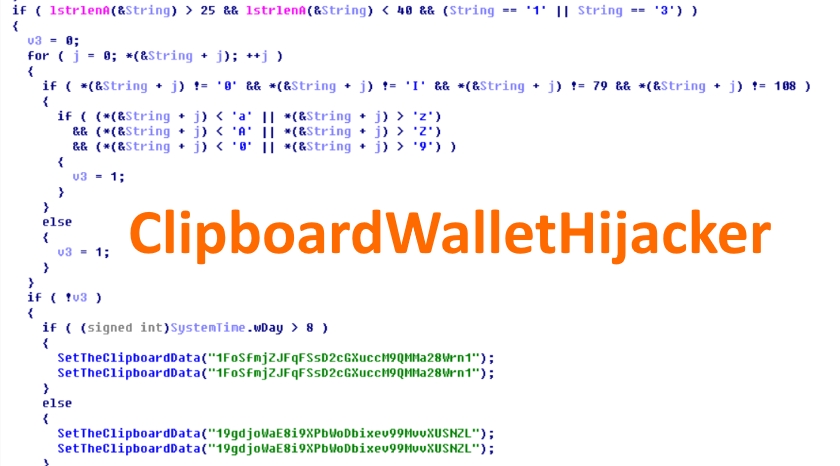
Malware replaces BTC & ETH addresses in the clipboard
The malware’s purpose is to intercept content recorded in the Windows clipboard, look for strings resembling Bitcoin and Ethereum addresses, and replace them with ones owned by the malware’s authors.
ClipboardWalletHijacker’s end-plan is to hijack BTC and ETH transactions, so victims unwittingly send funds to the malware’s authors.
The malware will use the following addresses when replacing strings in users’ clipboards:
BTC: 1FoSfmjZJFqFSsD2cGXuccM9QMMa28Wrn1
BTC: 19gdjoWaE8i9XPbWoDbixev99MvvXUSNZL
ETH: 0x004D3416DA40338fAf9E772388A93fAF5059bFd5
Checking the balances of these addresses using Blockchain.info (1, 2) and Etherscan.io, we can see crooks only received 0.12434321 BTC from eight transactions and no Ether. That’s around $800.
Since Qihoo 360 is a vendor with the vast majority of its presence on the Chinese market, it is believed that most of the 300,000 infected PCs are located in China and neighboring countries.
Other cryptocoin-related threats
But this is not the only cryptocurrency-focused malware campaign discovered these past weeks by Qihoo researchers.
They’ve also stumbled upon TaksHostMiner, a malware strain that infected over 10,000 computers in one day, and which mines cryptocurrency on infected hosts. This malware’s shtick is that it ceases operation when the user opens the Windows Task Manager.
Researchers also uncovered WagonlitSwfMiner, a coin-mining malware strain distributed via drive-by downloads that exploit an Adobe Flash vulnerability (CVE-2018-4878) to automatically infect victims.
Qihoo also discovered the Bondat IoT/Linux worm that spreads among web servers and IoT devices, infecting devices with a hidden cryptocurrency miner and also using infected devices to brute-force WordPress sites.
Source: bleepingcomputer.com